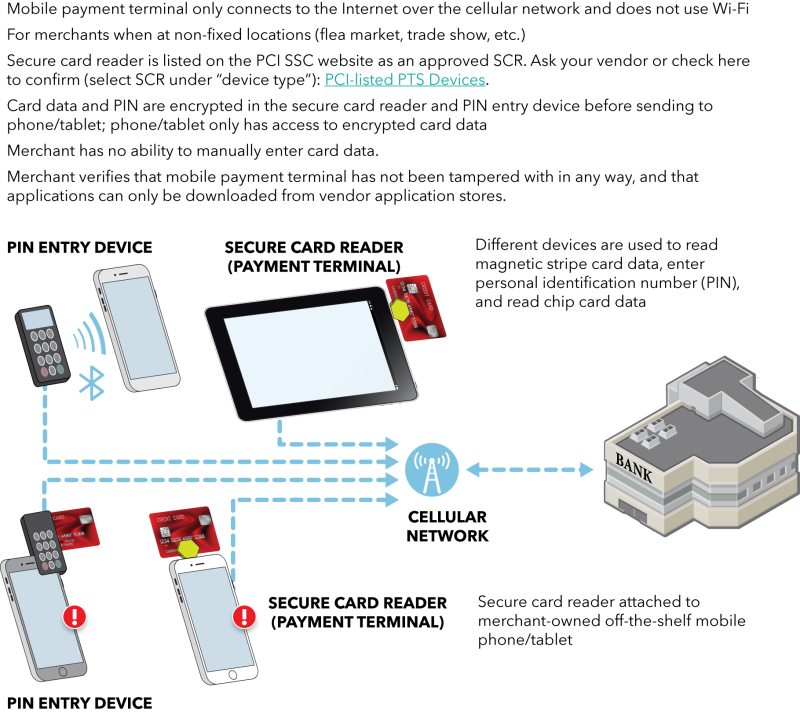
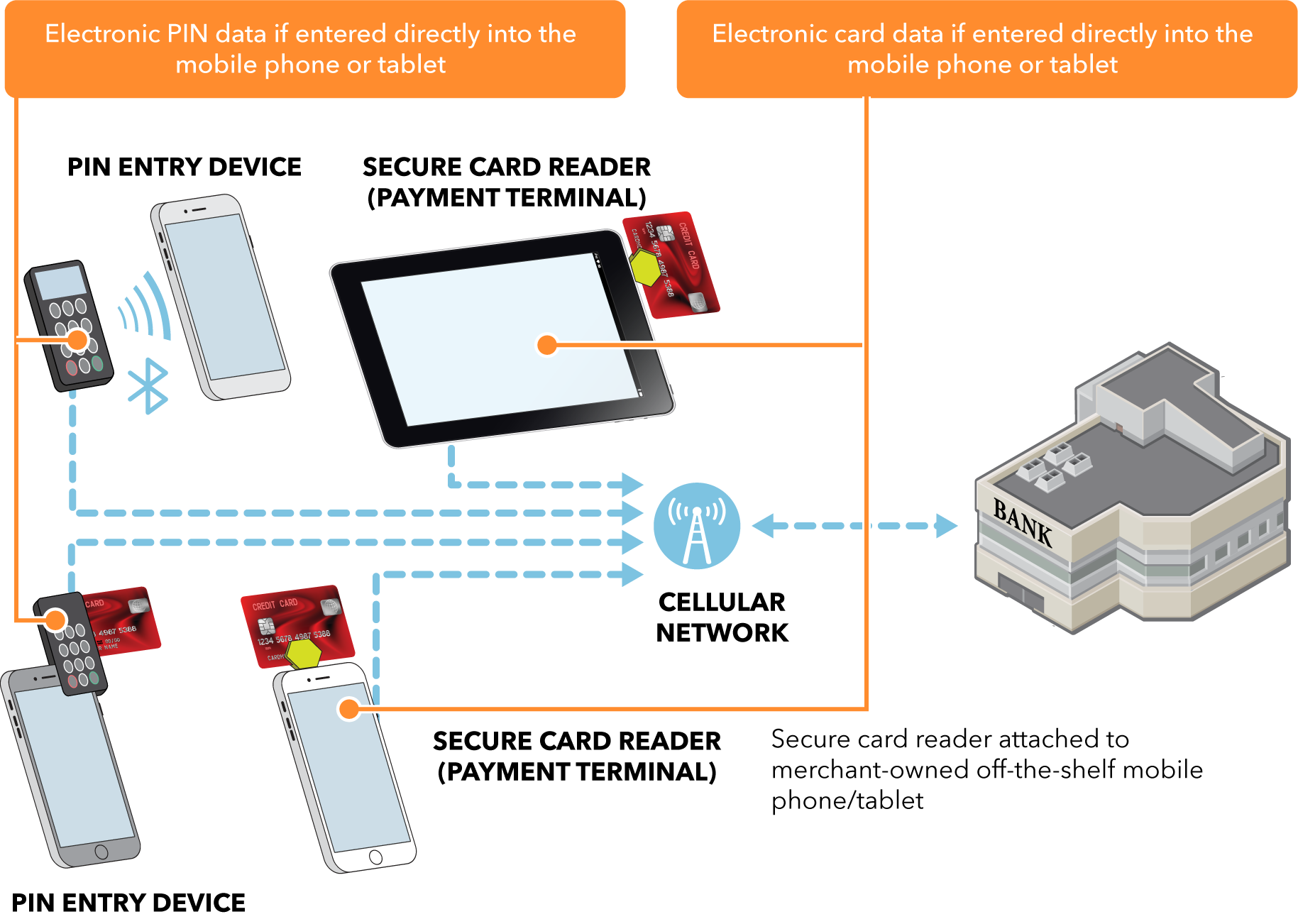
If you are using a PCI-listed Point-to-Point Encryption (P2PE) solution, go to Type 15.
Where is your card data at risk?
How do criminals get your card data?

How do you start to protect card data today?
Click on the icons below for the Guide to Safe Payments and information about these security basics. For simple definitions of payment and security terms, see our Glossary.

Ask your PCI Qualified Integrator & Reseller (QIR) or your hardware/software vendor for help

Use secure payment systems

Protect card data and only keep what you need

Protect in-house access to your card data

Protect all systems from the Internet

Regularly inspect your payment terminals for modification, changes, or other visual clues that suggest tampering or alteration

Limit remote access for your vendor partners – don’t give hackers easy access

Install patches from your payment terminal vendor

Make your card data useless to criminals

